What Statement Best Describes What Encryption Is
Cybersecurity Essentials 11 Final Quiz Answers 100 2018 Quiz Instructions This quiz covers all of the content in Cybersecurity Essentials 11. Which statement best describes a motivation of hacktivists.

Inf 103 Week 4 Quiz Social Networking Sites Powerpoint Presentation Online Learning
View the full answer.

. Network encryption sometimes called network layer or network level encryption is a network security process that applies crypto services at the network transfer layer - above the data link level but below the application level. Network encryption network layer or network level encryption. C Encryption only works.
The attacker could have captured the encrypted communication and stored it while waiting for an opportunity to acquire the key. ITC Chapter 1 Quiz Answers What three items are components of the CIA triad. Which statement describes the risk of not destroying a session key that is no longer used for completed communication of encrypted data.
Which statement best describes encryption. Data should always be kept encrypted since modern CPUs are fully capable of operating directly on. An encryption method in which two separate keys -- a private key and a public key -- are used to encrypt and decrypt a message Which term is used to describe an application that installs hidden services on a system that enables the attacker to monitor and control the operation of the system.
SEAL is a stream cipher It uses a 112-bit encryption key. Which of the following best describes the situation that allows an attack aimed at the identification of existing wireless networks the SSID used and any known WEP keys. 9 The following statement best describes encryption on the internet.
Which statement best describes configuring a NAT router to use dynamic mapping. It is an example of an asymmetric algorithm. Which statement describes a distributed denial of service attack.
It is easily seen but difficult to interpret. Which statement about encryption is True about data in use. Which statement best describes asymmetric-key encryption.
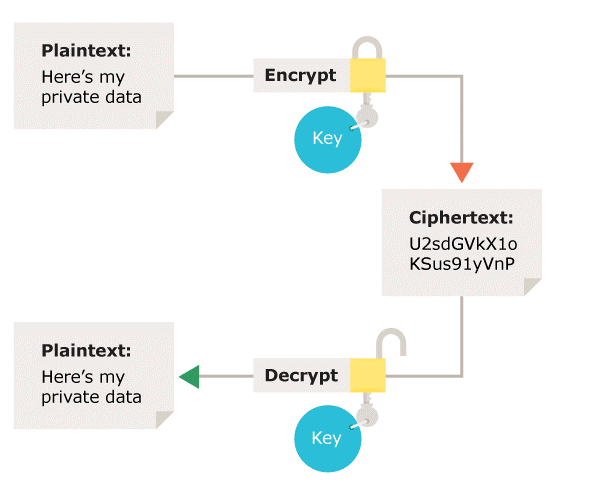
B Encryption assists in an overall security program. Decryption turns ciphertext into plaintext using a key. Confidentiality integrity and availability.
Asymmetric encryption is used for authentication non-repudiation and key agreement and exchange. What is another name for confidentiality of. Which statement describes the Software-Optimized Encryption Algorithm SEAL.
A software program designed to detect and block viruses from infecting your computer. It is software that secretly gathers information about users while they browse the Web. Encryption turns plaintext into ciphertext using a key.
O Encryption turns ciphertext into a key using plaintext. It is a guideline for information security for an organization. Encrypting only email messages containing sensitive information raises a flag to hackers pointing them directly to the messages that are most likely to contain valuable sensitive information the very information youre trying to.
A software program deliberately created to harm your computer. There are multiple task types that may be available in this quiz. Question 1 1 pts Which statement best describes encryption and decryption.
It is important to understand the characteristics of. Symmetric encryption is very fast and used for bulk encryption of large amounts of data. Encryption is a technical and data safeguard that converts clear text in a random set of characters.
The CIA triad contains three components. Spyware simply refers to a software with malicious behavior which gathers information about an individual or organization and then sends it to another entity in a way that causes harm. Choose three intervention availability scalability confidentiality integrity access Explanation.
It requires more CPU resources than software-based AES does. The network transfer layers are layers 3 and 4. Symmetric encryption is more efficient for bulk encryption of large amounts of data for transfer.
Encryption is an important technology used to protect confidentiality. Quizzes allow for partial credit scoring on all item types to foster Continue. Which statement best describes the Data Encryption Algorithm DEA Data Encryption Algorithm DEA is a widely-used block cipher encryption method using a private secret key Data Encryption Algorithm DEA is an algorithm used.
The statement that best describes spyware is A. A Encryption completely protects your data. Search for an answer or ask Weegy.
2 question Which statement best describes spyware. It is designed to test the skills and knowledge presented in the course. Best practices for email encryption include consistently encrypting all messages you send and receive.
The following statement best describes encryption on. Spyware infiltrates the computing device and. It is software that secretly gathers information about users while they browse the Web.
O Encyrption hides data in plain sight. A software program that secretly gathers information about users while they navigate the Internet. AES is an encryption protocol and provides data confidentiality.
The organization will need as many registered IP addresses as it has computers that need Internet access. Encryption is BEST described as a. DH Diffie-Hellman is an algorithm that is used for key exchange.

Itif Technology Explainer What Is Encryption Itif

Ccna4chapter7examanswersfor Securingsitetositeconnectivity 2020 Configrouter Exam Answer Encryption Algorithms Cloud Computing Services
No comments for "What Statement Best Describes What Encryption Is"
Post a Comment